Wifi Password List Txt
Feb 20, 2018 - Wordlists sorted by probability originally created for password generation. Top204Thousand-WPA-probable-v2.txt pre-release branch, Feb 19, 2018. Lists sorted by popularity will include `probable-v2` in the filename. Step-by-Step tutorial on how to hack UPC wireless networks with default password using Aircrack-ng suite, Maskprocessor and oclHashcat GPU on Windows. Home » Wifi Hacking Tutorials » How to hack UPC wireless networks and other WLAN pt 1. Maskprocessor A?u?u?u?u?u?u?u -o /usr/A.txt.
Compressed File Size: 4.4gb Decompressed File Size: 13gb Just thought i would share the link for those who are looking for a decent list to pen test their networks. The list contains 982,963,904 words exactly no dupes and all optimized for wpa/wpa2.
Would also just like to point out that this is not my work, instead it was a guy who compiled a whole load of useful lists, including his own to come up with 2 lists (one is 11gb and one is 2gb) i will be seeding this torrent indefinitely since it is shareware! INFO This is my final series of WPA-PSK wordlist(S) as you can't get any better than this!
My wordlist is compiled from all known & some unknown internet sources such as; 1. Coasts password collections 3. Xploitz Master Password Collection(s) vol 1 and vol 2 (official Backtrack 3/4/4R1 wordlist collections, Thanks Xploitz) 4. Ftp sites such as; & others 5.
All wordlists onand(as of ) 6. All wordlists hosted on; 7. All usernames from '100 million Facebook usernames and personal details' as leaked onto Torrent sites 8. All wordlists from the Argon (site now closed) And as a bonus my personal wordlist of 1.9 GB! Which also includes; My 'WPA-PSK WORDLIST 2 (107MB).rar' & 'WPA-PSK WORDLIST (40 MB).rar' Torrent & random usernames grabed from over 30,000+ websites such as youtube, myspace, bebo & outhers sites witch i can't mention.

He he ALL WITH NO DUPES OR BULL-SHIT AND IS FORMATTED TO WPA RULES OF 8-63 CHARS!! Hope you enjoy.:テつャ).
Wpa Wordlist Download
P.L.E.A.S.E S.E.E.D W.H.E.N. The Pirate Bay ISO Hunt Torrent Hound Hope this helps any one who is starting out and learning about pen testing and network security, and don't forget to seed for others!

I know for a fact that aircrack-ng cant take TO large files at once. Anyone have a solution for how we could split it into.
The text file i meen?:-)I made a 9+gb sequential numbers 00099999 file and aircrack used it fine, but I do see your issue, it would take days to crack something, so I used the linux split command (Read the help file) and made like a shit ton of 50mb files. Cracked the wifes wifi(which I already knew the range it was in since I told her that her boss was an idiot for using just numbers and only as long as 9 characters). I just did a head and a tail on the files, till I found which one I knew it was in, and it cracked in like 20 minutes on a crappy dual core laptop with BT5. Now that said, had I had to go and use the entire 9GB file, well, it would have done it, but would have had to run for days to go through all 8 characters, then all 9 until it found it. Split is your friend. So is sort if you want to sort unique or also, reverse the order of the list like say 1,2,3,4,5 becomes 5,4,3,2,1 (but with say a list of characters 8 or longer).
If I had it on my home machine and I sent the pcap to the hashcat site,I could have made a file compatible for cracking using oclhashcat on my GPU. That 9+GB sequential list probably would have cracked in an hour or so. Got to love GPU computing. BT5 has the ability to use CUDA and OpenCL drivers too, but they don't work on my POS laptop, but just a heads up, you can crack with the 13gb list if you split it into chunks and run them in parallel too if you've got more than one GPU.
I appreciate this list but I haven't had any luck with it. Does anyone know by chance if this include the passwords that are include in the famous renderman rainbow tables? I will be trying those next. For those new to WPA cracking I have a few short tips I learned alone the way.
Tip #0 is don't even bother unless you are using a graphics card to crack. For a long time, pyrit was the goto app for this. Pyrit is not very user-friendly. I wouldn't bother with it. It's given me nothing but headaches and fails to run properly on many machines I try to compile it on. The stripLive command works ok, but I'd veer clear of pyrit and focus on the tried and true classic aircrack-ng suite.
FIrst, always make sure you are sitting on one channel when collecting a handshake. Don't be hoppin, it won't work very well. So you have airodump-ng or kismet running on a single channel for a couple days or so. You can try to force some deauths using mdk3 or airreplay -0 or airdrop-ng, but why be a dick, just wait and let the handshakes come to you.
Best Wifi Password List
If you are in a hurry you can always use the mdk3 amok mode and nuke everyone around you for maximum collection power. I haven't thought of it till just now (prolly because it'd be illegal somehow) but you might able to wardrive around firing mdk3 on one card and sniffing using airodump on another and just vaccuum in handshakes. That's pretty evil, don't do it. Now you've got a big ass 2gig.pcap dump file filled with total crap. Beacons, broadcast traffic, you name it. You can extract juuuust the goodies with aircrack-ng -J outfile.cap. This will examine the pcap and show you where you have succesful handshakes captured.
You then save them to a tiny.hccap file strictly for use with ocl-hashcatplus. What a great program! I hate saying this- but it runs in windows perfectly! I loathe windows now but it's the only OS that can run my awesome zeroday new NVIDA card with hella CUDA cores. Before that program everyone was using pyrit for the cuda functionality and as I said, it's a pain. Aircrack-ng is not going to handle the massive dictionary files you want to use.
Download ocl-hashcat and read some tutorials about how to use it to crack your hccap file with your super duper 'Super WPA' file you grabbed from this post. Another note, the.rar.
File in this post is (I think) made with rar v3 or something, I couldnt get a successful extraction with 7zip. You'll need to download unrar.exe command line tool (for windows, not DOS) from the winrar labs site. Beware of any other RAR programs as they all seem to be bundled with malware these days.
You can also safely extract it in linux. It takes me about 6 hours to run through the SuperWPA dictionary at 44k hashes a second using a $400 video card.
That's actually pretty crappy performance for such an expensive card compared to some of the speeds I've seen posted online, but it's aight. Anyway, good luck. You'll need it. Edit: the new version of aircrack suports dictionaries over 2gb so it may work with this one. Not read this post in a while and am so glad all you guys got the use out of this. I thought i was setting it indefinitely but for some reason my utorrent crapped out, working on re adding the torrent without having to download it again. Also i would suggest using pyrit in kali / backtrack for using this list, or as shuttin mentioned aircrack might actually support a word list this size now.
I am going to be testing this word list using kali linux, i'll post the commands pkms etc to give you guys and idea of just what works best. I was googlein my wordlist and i found this, am rather flatterd, thanks guys for you comments and compliments. If anyone has any other comments or sugestions then you can email me ( my email is included in the torrent).
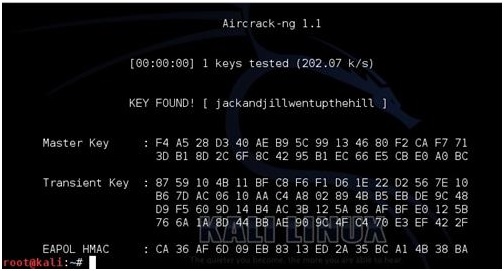
1 point i would like to mention, as i have sooooo many questions asking ' how do i open your wordlist?' Or 'Aircrack-ng says is blank' A1. You cant open it lol, no one has that amount of ram installed ay?, and why would you want to? A2 Aircrack-ng only supports files up to 2gb Max! So i would use Pyrit in backtrack and ditch aircrack-ng, its a little outdated. And pyrit can use GPU for more speed far more than most CPU could ever hope to accumpish. For ex: I have a Quad core, and a geforce 620 gtx and get around 13,000 pmks much faster than rubbish aircrack-ng, hears a pyrit chart to cmpair results for yourself.
And hear is some usefull wordlist manipulation commands to clean up your wordlists. Here are some useful commands to clean-up your wordlists (for WPA / Wi-Fi) (FOR BACKTRACK 5) 1. To remove all none compatible WPA word-lengths (8-63) cat yourwordlistfile pw-inspector -m 8 -M 30 yournewfile This will cut out all words that are NOT 8 - 30 letters in length and put them in 'yournewfile'. I know the max WPA length is 63 but 30 is more realistic for a potential password 2.
To join multi wordlist files cat file1 file2 file3. Etc newfile This would join file1 file2 file2 and put it in newfile 3. To remove all duplicate words cat wordlistfile uniq newfile 4. To remove all html shit, white space and none alphanumeric entries i.e.!' !ツ」'$%$$%^&.&(.)+ newfile 5.
To convert all to lowercase tr ':upper:' ':lower:' outputfile. Hak5 Fan you very welcome, glad it helped you out. For a point of reference, i noticed a lot of people banging on about rainbow tables, in my experience thy are a complete waste of time, bandwidth and hd space!. I saw one that was about 34GB in size and only had around 1000 words and was compiled ageist around 100 DEFAULT essids such as netgear, linksys.etc. Witch is stupid because default set wpa keys are random chars anywhere from 8 - 12 chrs long, so no dictionary in world would crack them. (usually can use reaver to crack pin tho:) ).
So thing to bare in mind is. Custom essid = custom wpa key.!
So much more the likely-hood of cracking them.:).